Often, the entry point of many cyberattacks is services that have not been secured. This can occur if you unintentionally leave your everyday end point device—such as a smartphone—open to different types of attacks, or if your apps and services only have a one-phase identification. These instances could result in attacks through your devices, which can lead to leaks of personal and business information.
The following are some easy steps that will help improve your security.
1. Authenticator App
Authentication is the first step in access control. To best secure our social media accounts and other services we use, it’s important to add a layer of protection to the sign-in process.
There are three common factors used for authentication:
Something you know
The “something you know” factor is the most common factor used and can be a password or a simple personal identification number (PIN). However, it is also the easiest to hack.
Something you are
This could be a fingerprint or other biometric method such as hand geometry, retinal or iris scans, handwriting, and voice analysis. While biometrics provide the strongest authentication, it is susceptible to errors. A false rejection error occurs when a system falsely rejects a known user. A false acceptance (although less common) error occurs when a system falsely identifies an unknown user as a known user. Biometric systems typically can be adjusted for sensitivity, but the sensitivity affects the accuracy.
Something you have
The “something you have” factor adds an extra layer of security to your account, such as a one-time number that you get from a handheld device or from an authenticator app. The number displayed on the token changes regularly, such as every 60 seconds, and the authentication server always knows the currently displayed number. If attackers have access to your password, they will not be able to log in because they will need the one-time number displayed in the app. The three most secure authenticator apps are Google Authenticator, LastPass, and Microsoft Authenticator.
2. Two-Step Verification for WhatsApp
Attackers targeting WhatsApp users can hijack their accounts by impersonating friends and requesting SMS security codes. This scam has been around for years, but by 2021, the attacks spread around the world. Continuing from the previous section where we talked about the importance of adding an extra layer of security by an authenticator app, in WhatsApp, the way to add a layer of protection is by two-step verification.
Multi-factor authentication (MFA) is a security measure that requires two or more proofs of identity to grant access. MFA makes it harder for cybercriminals to gain initial access to your account by adding more layers of authentication, requiring extra time, effort, and resources to break. Think of adding MFA to your account in the same way you might add a locked security screen to your home. It provides you with an extra layer of protection from criminals trying to break in.
Once MFA is set up, WhatsApp will periodically ask you to enter your PIN, so it is important to remember the code you have chosen.
3. Antivirus (AV)
Just like installing antivirus on a computer, it is recommended to install antivirus on any device with an internet connection. Smartphones are not immune from code injection by attackers and are therefore required to be protected by antivirus. Keep in mind that our smartphones are in daily use and contain all our most personal, business, and sensitive information—more than a personal computer.
The antivirus works on the smartphone as it works on the computer—it detects malware, spyware, abnormal traffic, etc. The top AVs for android are Avast Mobile Security, AVG Antivirus, Norton 360, and McAfee.
4. Disable Third-Party Apps
Downloading an application from a third-party app store can infect your smartphone or tablet with malicious software and could enable someone to take control of your device.
Apple AppStore and Google Play are the two biggest official app stores. Each platform includes native applications that are built for the iOS operating system or for Android devices. Both platforms also include third-party apps in their store. Third-party apps in the official app stores usually follow strict development criteria and are checked to make sure they do not contain malware. Google Play and the Apple AppStore continuously work to protect our devices and data and routinely remove problematic apps.
External third-party apps, however, which have not been tested and supervised by Google or Apple can potentially:
- Infect your mobile device with malicious codes like ransomware and adware. even the ads or codes can be “injected” into popular apps you might download through a third-party store.
- Sell or share your data with other parties.
- Copy and store your data on their servers and the data could be stolen from there.
- Make it tough for you to delete your data.
If you decide to download apps from a third-party store instead of an approved store, we highly recommend you compare hashes prior to installation.
To avoid installing third-party apps, it is necessary to regularly block the download option of these apps as shown below:
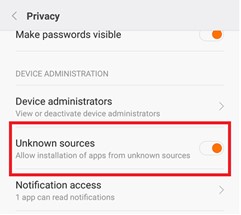
5. The Dangers of Public Wi-Fi
Free internet access is very appealing, especially when you are traveling abroad, and data SIM cards are expensive. Public Wi-Fi is usually free internet that can be found in popular places like airports, coffee shops, malls, restaurants, and hotels. However, it could be risky to use public Wi-Fi when you log on with your username and password to check your social media account, read an email, or check your bank account.
The first risk is that these public networks often lack security. The second risk is a common threat called a man-in-the-middle (MITM) attack. When a computer connects to the internet, data is sent from point A (smartphone) to point B (service/website), and an attacker can get in between these transmissions without anyone noticing and “read” them. In effect, everything that happens in this communication range is exposed and can be passed on to third parties that can trade the information. The third risk by sophisticated attackers is to make victims connect to Wi-Fi that seems like a legitimate network.
Our recommendation is to never connect to a public network. However, if this can’t be avoided, you need to secure your information by using a virtual private network (VPN) to make sure your connections are private.









