Mastering CTEM with Cye platform’s Exposure Assessment and Mitigation
Learn how Cye platform can help you master continuous threat exposure management (CTEM) so you can make better security decisions.
DOWNLOAD NOW
Cye platform evaluates all findings and attack routes to determine which vulnerabilities are the most critical to block. Findings are prioritized according to importance and exposure; those that present a risk to critical business assets, and those most likely to be exploited. These are tagged as "critical to block."

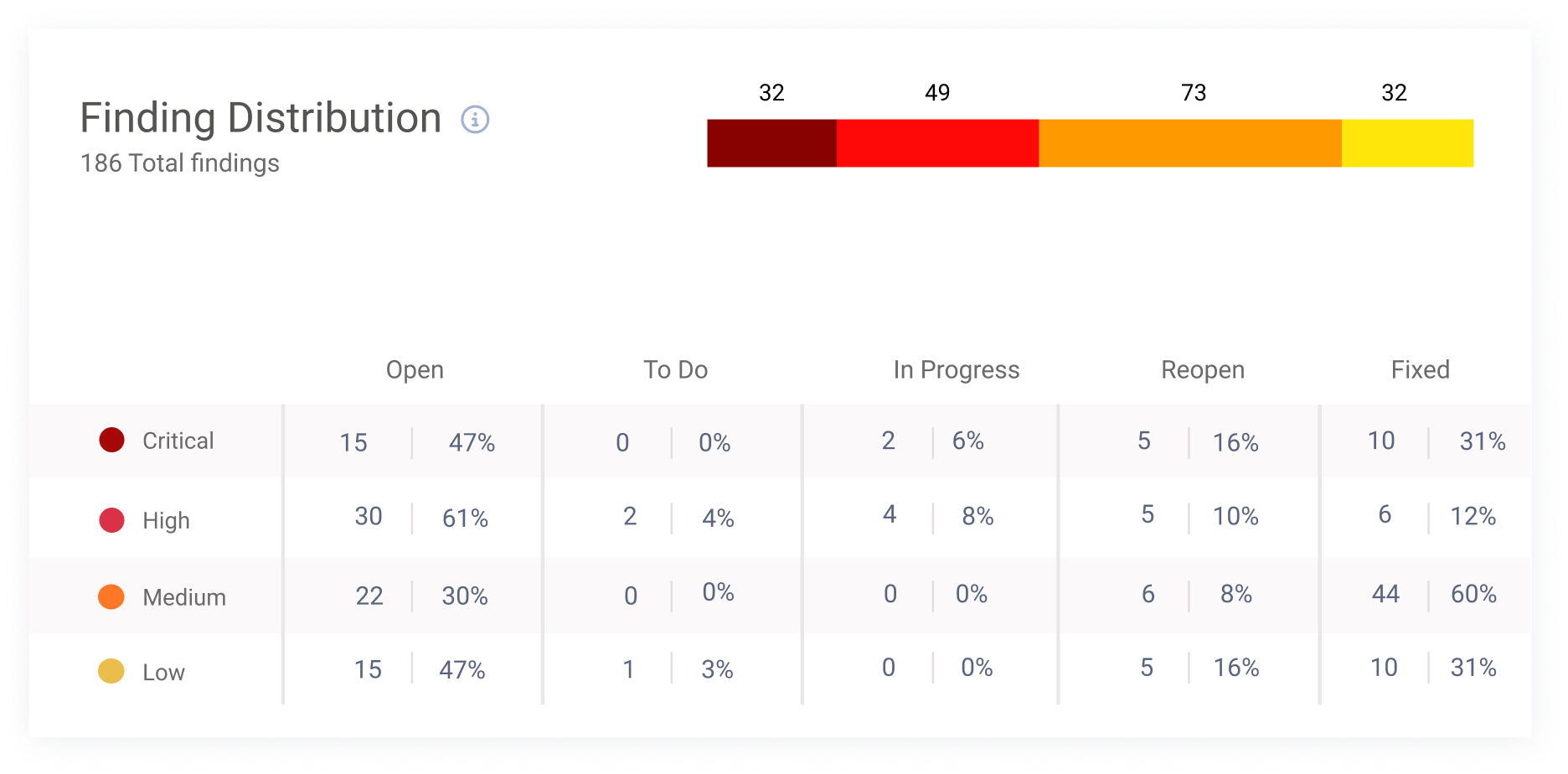
Cye platform focuses on vulnerabilities and misconfigurations based on a combination of data points. This enables organizations to create mitigation plans with clarity about exposure reduction, expected time to remediate, and team effort.
With Cye platform’s mitigation planner, you can mark specific findings on the graph as fixed to see their effect on attack routes. This visibility tool helps you mitigate findings most efficiently according to severity, budget, and time.


Cye platform creates four mitigation plans to help you understand the ramifications of mitigation: critical to block, most probable route, lowest cost level, and lowest effort level. Each one simulates the problems to be fixed, along with their cost and effort implications, allowing you to make the most optimized mitigation decisions.
Cye experts are with you every step of the way to offer mitigation guidance and advice. Our team will show you how to achieve the most effective results while considering your organization’s particular circumstances and budget.

