What is Vulnerability Prioritization?
Not all vulnerabilities are created equal. Some are harmless misconfigurations, while others could bring your business to a halt. Security teams need a way to tell the difference.
Vulnerability prioritization is the discipline of ranking remediation efforts based on two dimensions: likelihood of exploitation and business impact. In practice, that means mapping technical severity to financial and regulatory outcomes – so when engineering time is limited it’s focused on closing the highest-risk attack paths first – producing measurable risk reduction.
Priorities differ depending on an organization’s size, sector, and regulatory exposure. A Fortune 100 retailer, a digital-native scaleup, and a regional bank all face different stakes and service level expectations. The question isn’t just which critical issues exist, but which ones move the needle – in avoided breach cost, reduced downtime, protected revenue, and compliance posture (e.g., NIS2 in the EU, DORA for financial services, and SEC cyber disclosure requirements for U.S.-listed companies). By adding business context attribution – such as ownership, asset criticality, data sensitivity, and revenue/process linkage – a simple list of CVEs becomes an outcome-oriented roadmap.
How the Vulnerability Management Process Works
Effective vulnerability management follows six steps: inventory, classification, attack path analysis, prioritization, remediation, and continuous monitoring. Each step builds toward a program that focuses resources on what matters most and proves risk reduction.
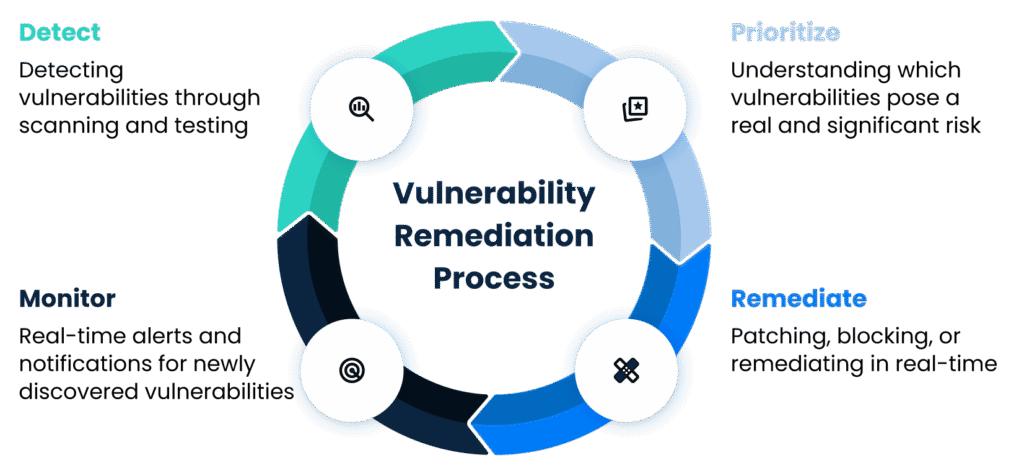
Step 1: Asset Inventory & Discovery
ou can’t mitigate what you can’t see. Start by building a living inventory of business-facing assets – with owners, environments, data flows, and connectivity to external attack vectors. Make sure to include cloud resources (both production and non-production), customer data stores, financial systems, and proprietary code repositories.
To measure progress, track KPIs such as:
- Asset Coverage: percentage of internet-exposed and crown-jewel assets inventoried
- Ownership Certainty: percentage of assets with confirmed owner & business units
- Unknown → Known Trend: net-new unmanaged assets identified each month
A recent study of over 2,000 cybersecurity leaders revealed that 74% had experienced security incidents due to unknown or unmanaged assets. That’s why asset inventory should be treated as the living blueprint of your security program, not a one-off project.
Step 2: Vulnerability Classification
Once the assets are properly identified and documented, you can begin to classify them based on exposure level and business function. Vulnerability scoring systems, such as the Common Vulnerability Scoring System (CVSS), provide a baseline by assigning scores based on severity and risk. While useful as a starting point, CVSS alone isn’t enough. To prioritize effectively, enrich these scores with threat-centric metrics (e.g., exploit availability, social prevalence) and environmental factors (e.g., reachability, data sensitivity, blast radius).
Metrics that Matter:
- Context Enrichment Rate: percentage of vulnerabilities enriched with CVSS score, exploit signal, and asset criticality
- Reachability Index: percentage of high/critical vulnerabilities that are reachable from the internet or partner networks
- Regulatory Mapping: percentage of vulnerabilities tied to systems in scope for NIS2.DORA, or SEC disclosure requirements
Step 3: Attack Path Analysis
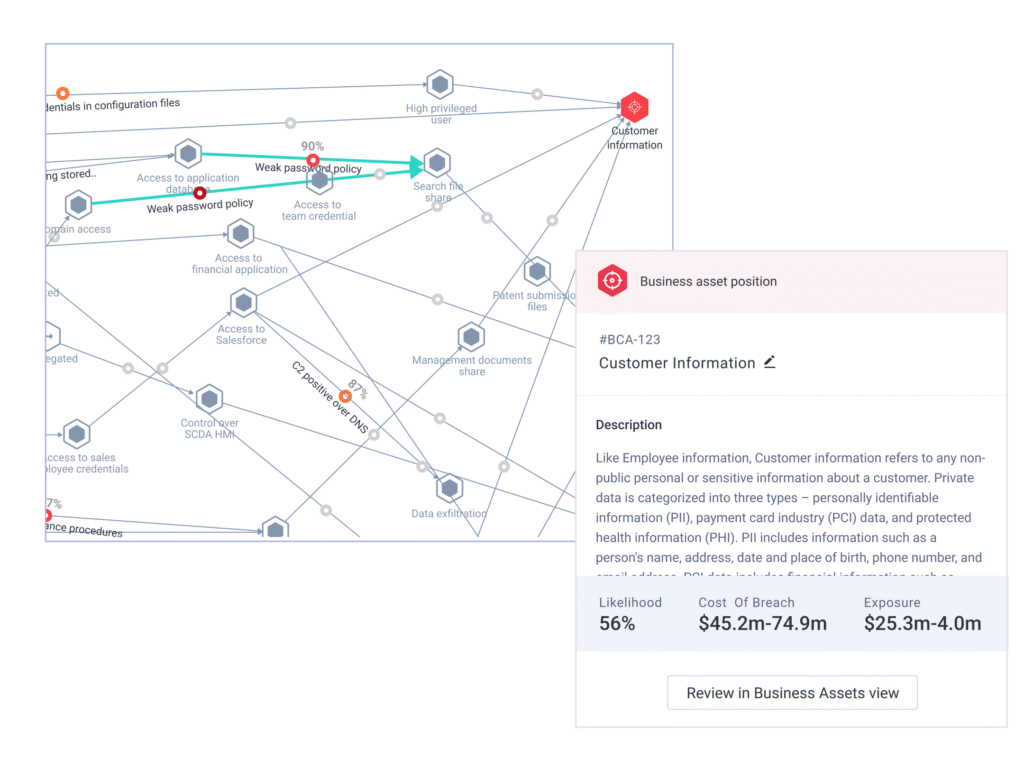
Context turns noise into a plan. Attack path analysis shows how an adversary can traverse from an initial foothold to creating a real business impact – for example, exploiting a misconfigured IAM role to reaching a data store containing EU customer records.
Key questions to ask include:
- How reachable is the asset from external entry points?
- What financial or regulatory consequences would follow if this path was exploited?
- Which employees, third parties, or SaaS integrations increase path reliability?
These insights outweigh a raw score because they quantify the path-to-impact: IP theft, payroll exposure, data-exfiltration penalties, outage costs, and cross-border reporting obligations (e.g., NIS2 incident reporting, DORA operational resilience, and SEC Item 1.05 Form 8-K timelines for material incidents).
Track KPIs that show real risk reduction, not just vulnerability counts:
- Path Elimination: percentage of exploitable paths to crown-jewel assets removed each quarter
- Mean Time to Risk Reduction (MTTR): average time from detection to path neutralization (beyond just patching)
- Potential Loss Avoided: modelled breach cost avoided based on closed paths and the value of assets at risk
Step 4: Prioritize High Severity Vulnerabilities
n attack path analysis will help guide your remediation efforts in the right direction and provide deeper context for vulnerability prioritization. Each asset has an assigned score and path of attribution that can be traced back to its owner, business function, and level of exposure.
With attack-path context, prioritization becomes deterministic. By tagging each vulnerability with asset criticality, owner, business function, and reachability, remediation can be scheduled by risk-per-day rather than raw counts.
Metrics that Matter:
- High-Risk Backlog Burn: percentage reduction of exploitable, business-critical vulnerabilities month over month
- SLA Adherence: percentage of high/critical issues on crown jewels remediated within target windows (e.g., 7 or 30 days)
- Regulatory Exposure Window: average number of days high-risk issues persist on systems in-scope for NIS2, DORA, or SEC requirements.
Step 5: Vulnerability Remediation
This is where priorities become measurable risk reduction.
Assign accountable owners per asset group, define timelines, and track progress. Remediation isn’t just patching; it can also mean compensating controls, hardening, network segmentation, or identity policy fixes that break the path faster than a full change cycle.
Metrics that Matter:
- Time-to-Compensate: average time to deploy a control that neutralizes exploitability
- Change Efficiency: percentage of changes that reduce multiple attack paths at once (choke-point fixes)
- Failure Rate: percentage of remediation attempts that require rollback
Step 6: Continuous Monitoring
Progress doesn’t end with remediation – it needs to be tracked and monitored over time. Effective continuous monitoring means benchmarking threat exposure metrics to get the most out of your vulnerability management program and demonstrating ongoing security gains.
Metrics that Matter:
- Exposure Score Trend: quarter-over-quarter reduction in externally reachable high-risk findings
- Detection-to-Neutralization: average time from new exploit signal to effective mitigation
- Third-Party Risk: percentage of critical vendor-connected paths that are continuously monitored and controlled
Vulnerability Prioritization Challenges
Lack of Business Context in Addressing Vulnerabilities
Mitigation without context is like playing vulnerability roulette – pouring security resources into fixing issues that might have no financial implication to the business. Every patch, configuration change, or control carries a cost: developer time, potential downtime, change windows, and stakeholder coordination. Unless that effort is tied to a business process, data class, revenue stream, or regulatory obligation, it’s impossible to demonstrate security ROI or justify trade-offs.
The answer is to map vulnerabilities to owners, assets, and processes first, then quantify the downside of inaction in terms of outage minutes, potential fines, revenue-at-risk, and loss of customer trust. According to the 2025 Vulnerability Statistics Report, over 33% of discovered vulnerabilities were rated critical or high severity. Without context, you can’t distinguish which of these discovered vulnerabilities yield the best returns if mitigated. As Warren Buffett said, “Risk comes from not knowing what you’re doing.” In cybersecurity, it’s not knowing what you’re protecting – and that’s a huge gamble indeed.
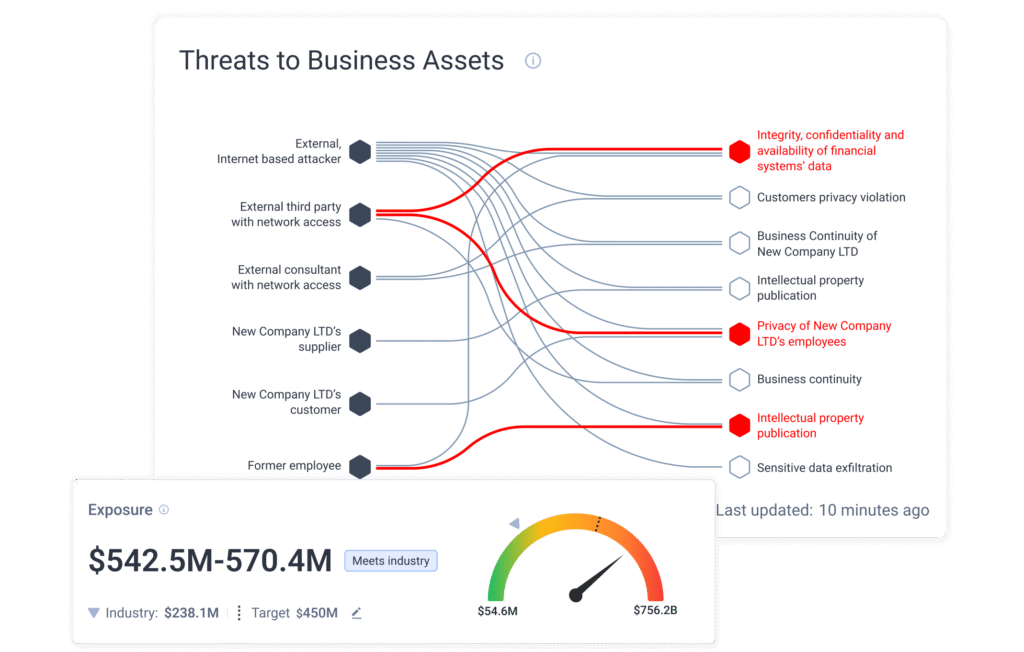
Multiple vulnerabilities with the same CVSS score may exist on different assets, one on a public-facing production server supporting revenue-generating applications, and another on a test system with no sensitive data. Although the CVSS score might be critical, the impact and outcomes are completely different. Treating them equally during mitigation planning would be counterproductive and inefficient, ultimately increasing your threat exposure surface by diverting valuable resources away from protecting your most critical business-facing assets.
Limited Threat Intelligence Data
Cyber threat intelligence (CTI) data comes from multiple sources, including open-source intelligence (OSINT), MISP (Malware Information Sharing Platform), dark web monitoring, private Slack and Telegram groups, vulnerability databases, and commercial threat intelligence providers. With this wealth of information comes a flood of data to ingest, especially from open-source communities, where the source quality can be slightly inaccurate or questionable at best.
Threat intelligence feeds can easily overwhelm security research teams with false positives that are treated as noise, enabling critical vulnerabilities to slip through the cracks without proper classification. Any of these overlooked threats can compromise systems and evade detection, especially if they haven’t been publicly disclosed or labeled as high-priority.
Vulnerability Scores Aren’t Always Accurate for Your Business
There is a current backlog of 25093 CVEs awaiting analysis from the National Vulnerability Database (NVD). Backlogs in public analysis pipelines and uneven metadata quality mean the numbers you see may lag behind the risk you actually carry. A seemingly minor misconfiguration might provide a direct route to regulated data, while a high-CVSS item could sit safely behind strong controls and pose little real-world threat. Relying exclusively on static scores delays action where it’s most needed, and inflates remediation workloads without reducing incident likelihood. A smarter approach is to combine technical scoring with exploit availability, control effectiveness, asset criticality, and attack-path reachability. This helps you act before formal scoring catches up – shrinking exposure on assets that would drive material impact, disclosures, or fines.
Since February 2024, the NVD has put the brakes on its analysis of published Common Vulnerabilities and Exposures (CVEs).
The impact has been significant: 42% of CVEs lacked critical metadata such as Common Vulnerability Scoring System (CVSS) or Exploit Prediction Scoring System (EPSS) during the delays, drastically impacting remediation efforts. In practice, this means that new threats exploited in the wild may go unnoticed for long periods, only to resurface once attackers have refined their TTPs and methodologies, leaving security teams far behind in terms of effective mitigation strategies.
Shadow IT and Unknown Assets
Shadow IT refers to employees using tools or applications without the knowledge or approval of security teams. What may feel like a shortcut for convenience or productivity can open the door to critical vulnerabilities. According to Gartner, “By 2027, 75% of employees will acquire, modify or create technology outside IT’s visibility, up from 41% in 2022.” These unsanctioned applications often request broad read/write permissions, potentially exposing sensitive company data, customer records, or internal systems. Worse, they create blind spots – vulnerabilities that security teams cannot detect or defend against simply because they don’t know they exist.
This risk extends to offboarding employees as well. Even with sanctioned applications, transferring or revoking access can be complex and time-consuming. With shadow IT, credentials may remain active and sensitive data may linger in unmanaged environments, creating long-term vulnerabilities that are invisible until it’s too late.
Vulnerability Prioritization Best Practices
These challenges are real, but they can be overcome with structured best practices.
Conduct Routine Risk Assessments
Move from annual audits to continuous, risk-based reviews that align with business change. Each assessment should validate the asset inventory, confirm ownership, and test for reachable paths to crown-jewel data and services. Quantify potential loss using impact models tied to revenue, operational disruption, contractual penalties, and regulatory consequences. Use the results to set clear SLAs by asset tier, define budget asks, and demonstrate how prioritized fixes shrink exposure over time.
Research shows that 1 out of 3 breaches goes undetected. A risk assessment can get to the root cause of a potential breach by identifying misconfigurations in cloud environments or other gaps in security controls that attackers can exploit.
Incorporate Red Teaming
The best way to prevent an attacker is to think like one. Red team exercises expose how an attacker could move laterally through the network and ultimately access critical business assets. You’ll also understand if your existing security tools are effective at preventing unauthorized access attempts and other attack techniques.
Red teamers can uncover hidden vulnerabilities that have yet to be disclosed or cataloged by traditional vulnerability scanners or public databases like CVE.
Prioritize Critical Vulnerabilities with Business Context
Make business context the gating factor for remediation. For each vulnerability, attach owner, asset criticality, data class, regulatory scope, exploitability, and path reachability. Prioritize by risk-per-day and choke-point leverage: prefer changes that collapse several paths at once over isolated patches. When patching takes time, deploy compensating controls – feature flags, WAF rules, conditional access, or segmentation – to cut the path quickly while engineering readies a durable fix. Report progress in executive terms: exposure reduced, outage minutes avoided, potential loss avoided, and compliance exposure window closed for in-scope systems.
Your CFO doesn’t need to understand the intricacies of a Continuous Threat Exposure Management (CTEM) platform or other vulnerability prioritization tools, but they certainly must understand the financial implications of security incidents without these essential tools and processes. Vulnerabilities must have a monetary value attached to them.
That’s where having business context helps put real numbers behind every risk.
Mitigate Business Critical Vulnerabilities Faster with Hyver
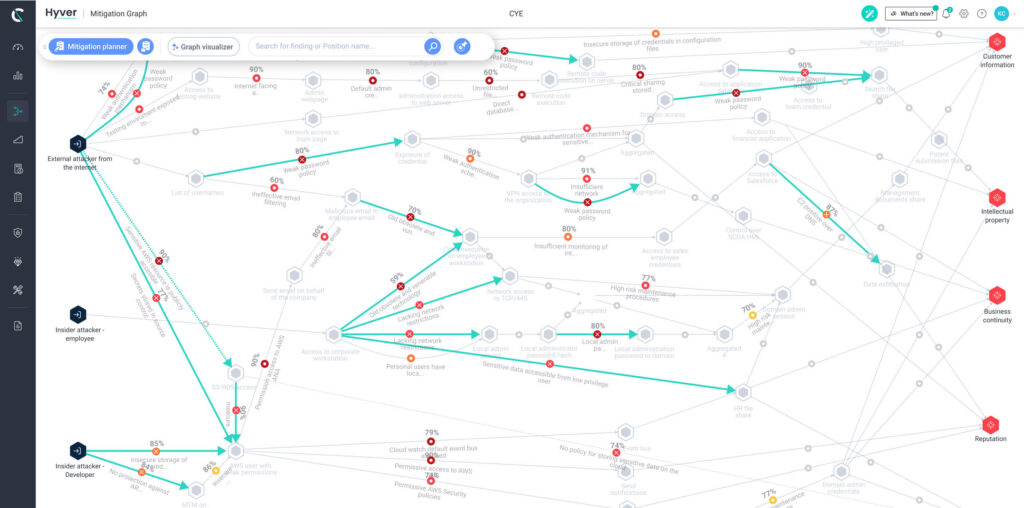
Vulnerability prioritization is a continuous process. CYE makes the process more efficient. CYE’s Hyver platform maps possible attack routes to your business assets across all environments, providing you with full visibility and traceability into all potential attack vectors with a graph model connecting the various security dots to the source at risk.
Hyver also assigns a monetary value to each vulnerability, enabling you to prioritize mitigation actions that deliver the highest return on investment and reduce overall threat exposure.
Want to learn more about how CYE can help you manage your organizational exposure? Contact us.










