Cybersecurity budgets are increasing, yet overall organizational cybersecurity maturity levels are – at best – remaining stagnant, or – at worst – decreasing, leaving organizations increasingly exposed to cyber attacks.
After analyzing this phenomenon, we came up with the following conclusions to help organizations increase their cyber resilience:
- Ditch compliance-driven cybersecurity maturity programs – While compliance is an important part of cybersecurity, it is certainly not enough. The compliance-driven approach applies a “one size fits all” to different organizations, which is not enough to cover the specific and unique challenges of each organization.
- Shift from using assessment to validating the program to building the program – Instead of starting with a template or compliance-driven approach and testing it at the end of the process, we believe that organizations must do it the other way around: they need to be able to identify weaknesses and vulnerabilities, set the targets and optimize how they build a cybersecurity program to make sure they are taking into account all relevant threats. Additionally, decision-makers need to be able to see the ROI and understand their investments and how the cybersecurity program is reducing the organizational risk and improving their level of resilience.
Watch the recording: The Data Your Security Program Needs
CYE’s model to achieving data-driven security decisions
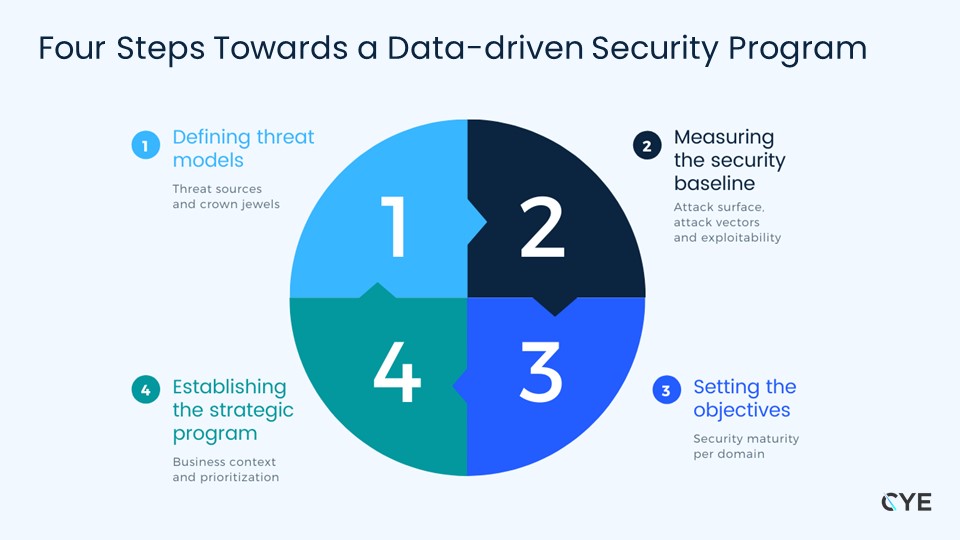
1. Defining the threat sources and crown jewels
Organizations need to be able to identify where their vulnerabilities lie, which business-critical assets they want to protect most and the attack routes that lead to the business’s crown jewels.

Frameworks and algorithms, such as the Max-Flow Min-Cut Theorem from Graph Theory in computer science, help solve this complex optimization problem. When it comes to cyberwar, CISOs need to focus their efforts on the areas that matter most. They need to be able to map out and calculate which routes, if breached, can derail an entire business operation and what is the best way of securing the routes that put the business at the greatest risk for attack.
2. Measuring the security baseline
There are multiple ways of measuring the security baseline, including risk evaluation, risk profiling, penetration testing, red, blue and purple team exercises, and so on. At the end of the process, however, organizations need to understand which threat sources can access which business-critical assets. They need to ask what the best way is of achieving that and, most importantly, how those vulnerabilities are connected to draw a specific risk map of the organization? Organizations then need to be able to understand the likelihood of each vulnerability being identified and exploited.
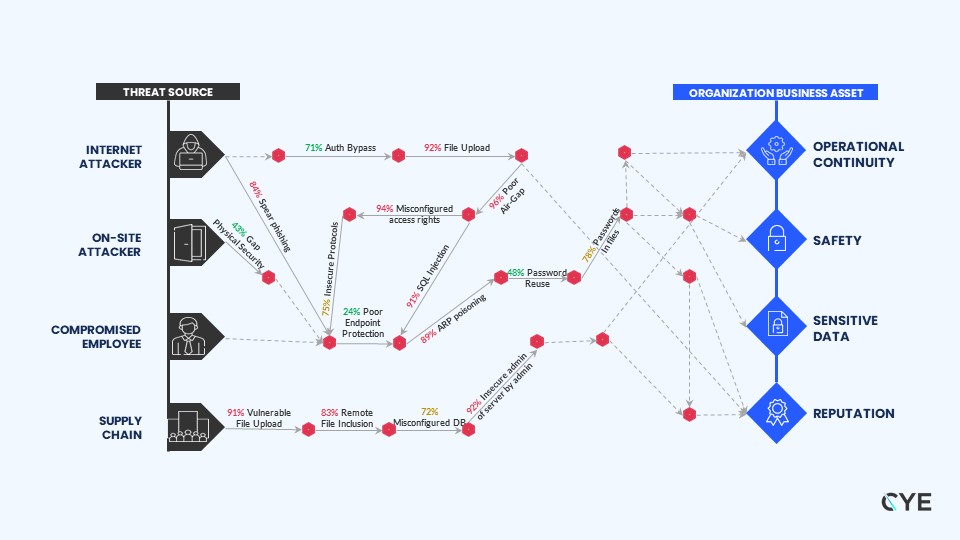
We believe that organizations should stop focusing on specific vulnerabilities and instead focus on complete attack routes. When looking at mitigation plans, the important part is eliminating attack routes, not eliminating vulnerabilities. If the vulnerability is mitigated, for example, but the attack route still exists, that does accomplish much. However, if vulnerabilities still exist, the attack route is eliminated, significantly increasing the organization’s cyber resilience.
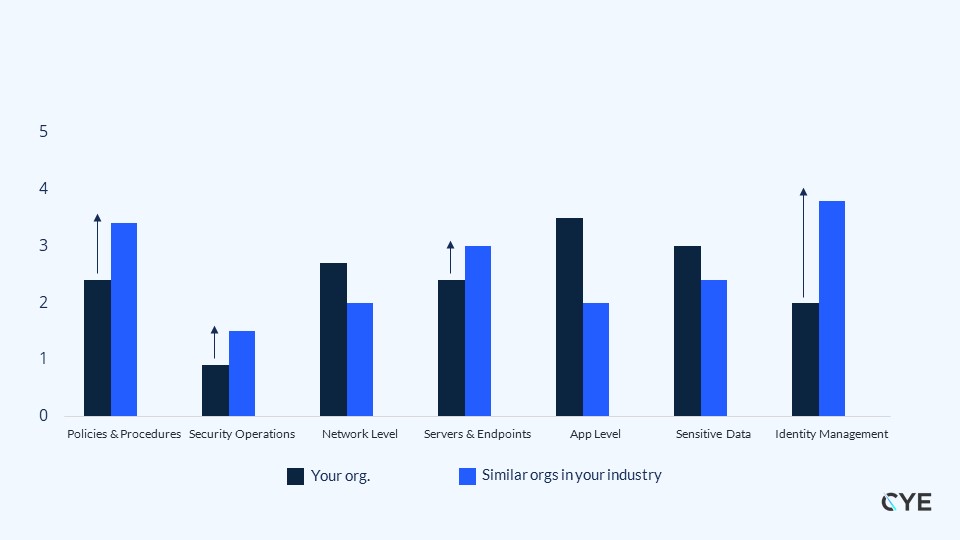
3. Setting the objectives
While there are multiple standards in the market to calculate cybersecurity maturity levels, such as CMMI and CMMC, we take a different approach by separating the different security domains in the organization to evaluate them one by one. We calculate each security domain by measuring the security level of the organization and benchmarking it against industry standards, geolocation and company size to understand where other organizations rank in the same security domain. If we see, for example, that an organization is below average in the industry, we take the industry, add one standard deviation above the average, and make that the maturity level goal that we seek to achieve.
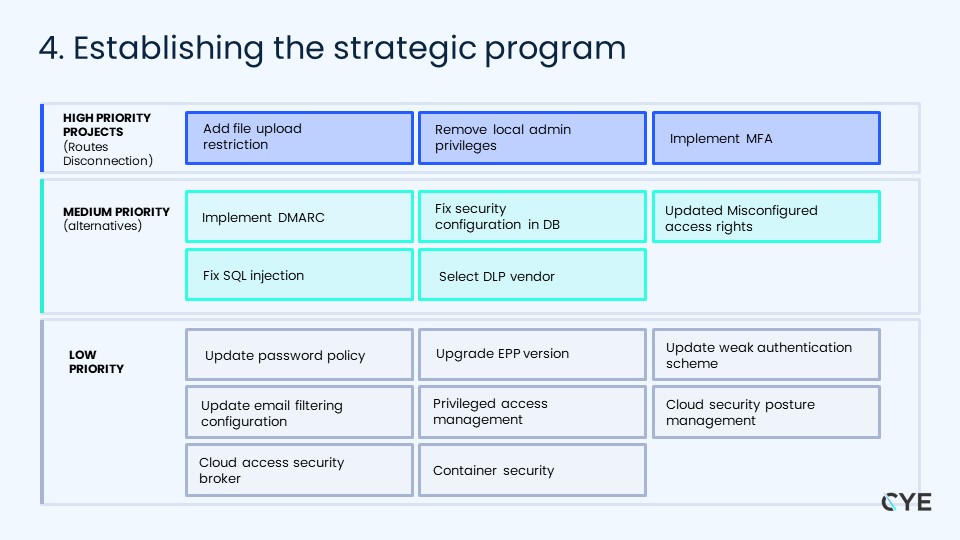
4. Establishing the strategic program
We created a mathematical structure, which enables us to identify the most probable attack routes and prioritize them based on the likelihood of them being exploited. We can calculate and quantify the specific risk reduction that was associated with the attack route. This can provide a clear mathematical evaluation for the cybersecurity risk of the organization, as well as the cost of potential damage and the cost for mitigation that is associated with the plan.
Ultimately, our unique approach:
- Takes cybersecurity from compliance-based to fact, data and mathematical based
- Ensures that mitigation and cybersecurity programs are tailor-made per organization
- Starts with identifying gaps and then tailoring the solution – not vice versa
- Identifies real attack routes and mimics actual hackers – without making assumptions
- Focuses on attack routes, rather than specific vulnerabilities
- Takes the technical impact of cybersecurity to business impact of cybersecurity
With the attack surfaces increasing exponentially and the rapid pace of changes in the external and internal threat landscapes, cybersecurity assessments must be conducted on a continuous basis, using a mathematical approach that ensures that your organization is not only compliant with regulatory standards, but is actually improving and fortifying its cybersecurity maturity score.









