Mastering CTEM with Cye platform’s Exposure Assessment and Mitigation
Learn how Cye platform can help you master continuous threat exposure management (CTEM) so you can make better security decisions.
DOWNLOAD NOW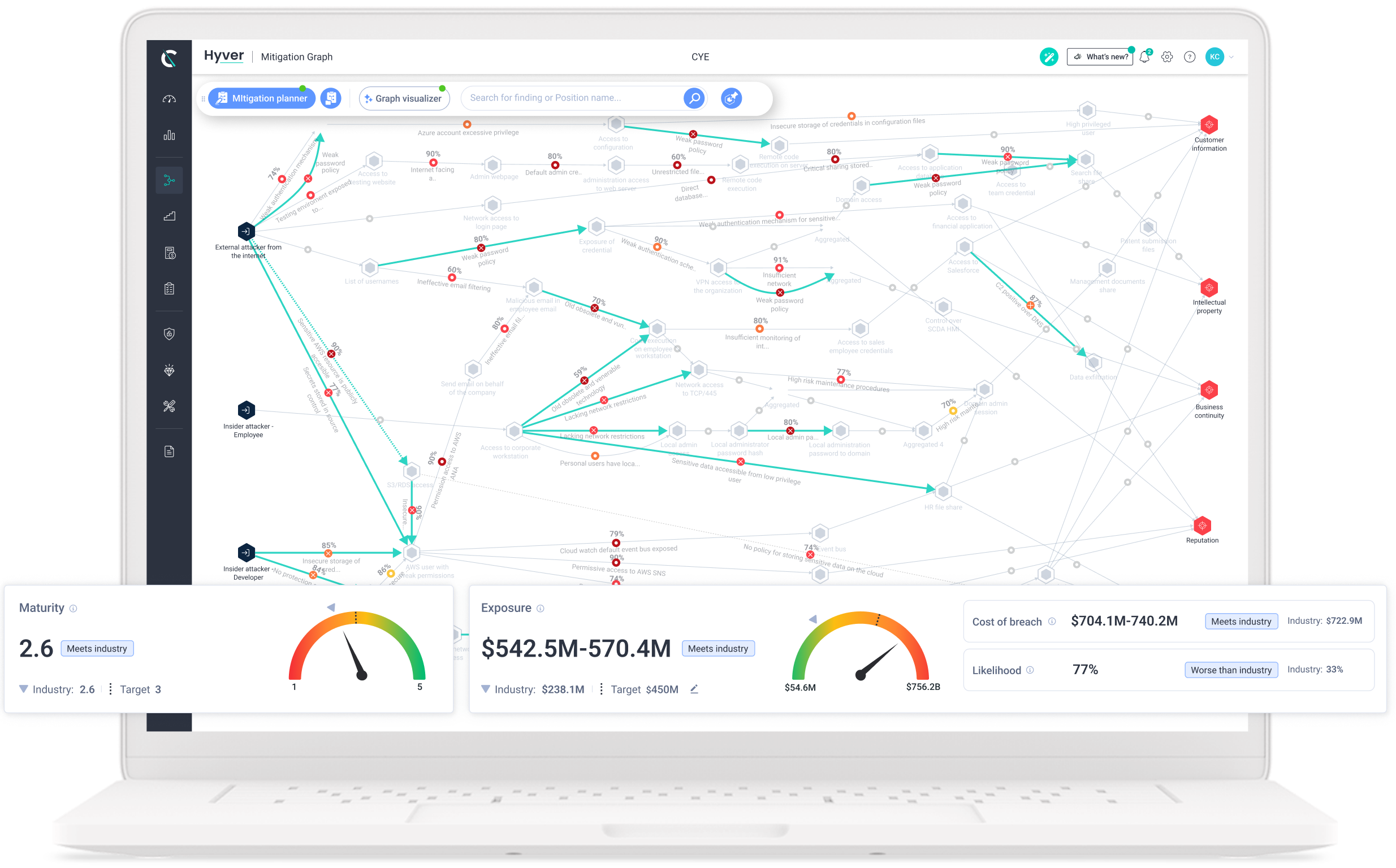
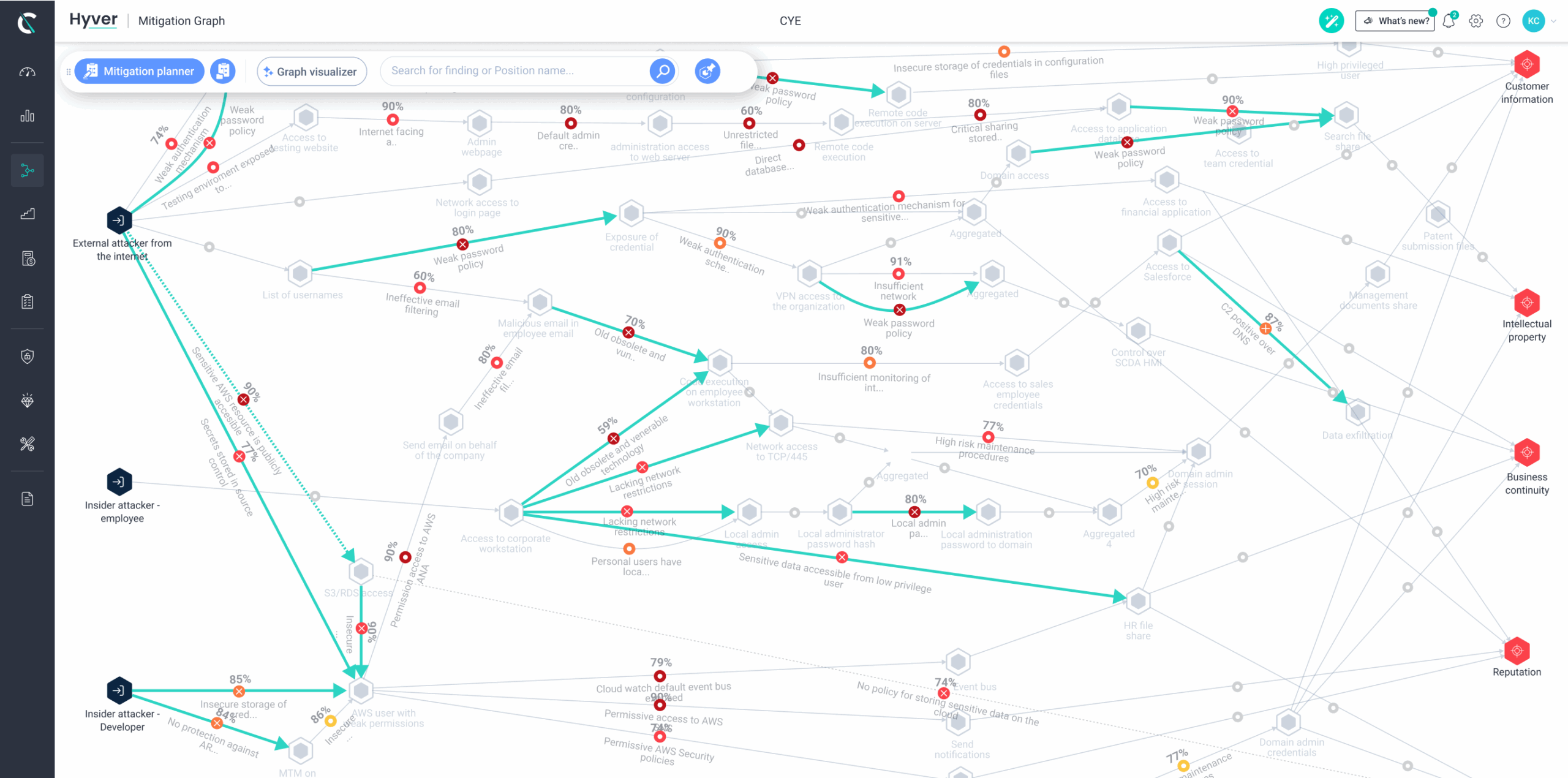
Cye Platform maps possible attack routes to your business assets across all environments. It delivers a complete, visual view of your organizational security posture.
By correlating asset value, the likelihood of attack, threat actor activity, and financial data, Cye Platform provides a dollar value of the cost of a breach compared to the cost of remediation.
Cye Platform provides a mitigation plan with clear prioritization according to business KPIs like security maturity and financial impact. That way, you can easily understand your security gaps and how to close them.
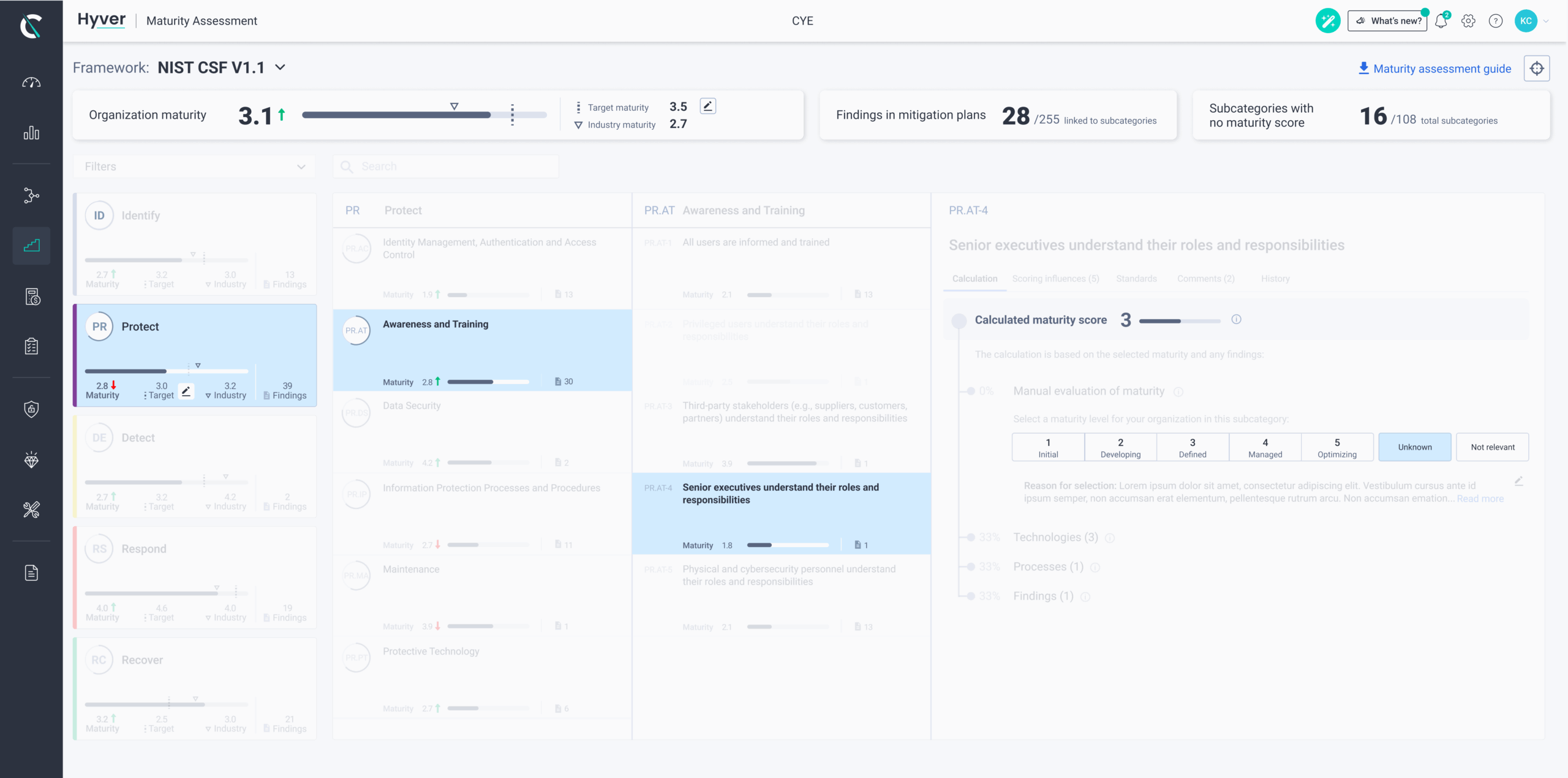
Cye Platform’s cybersecurity maturity assessment evaluates your organization’s overall cybersecurity capabilities and readiness using Cye’s continuous and objective data, as well as your security team’s input.
Empower your team to proactively identify and prioritize cloud risks, fostering alignment and collaboration among security, DevOps, and engineering.
Cye Platform integrates with leading security tools, enabling seamless data sharing and enhanced threat detection, which helps optimize your cybersecurity strategy and response efforts.





Agentless deployment with minimum effort to implement.

Features, workflows, and integrations are tailored to your organization’s specific needs.

Reliable information ensures informed decision-making to enable proactive cyber exposure management.

Benefits include enhanced operational efficiency, reduced costs, and improved security posture.
