Mastering CTEM with Cye platform’s Exposure Assessment and Mitigation
Learn how Cye platform can help you master continuous threat exposure management (CTEM) so you can make better security decisions.
DOWNLOAD NOW
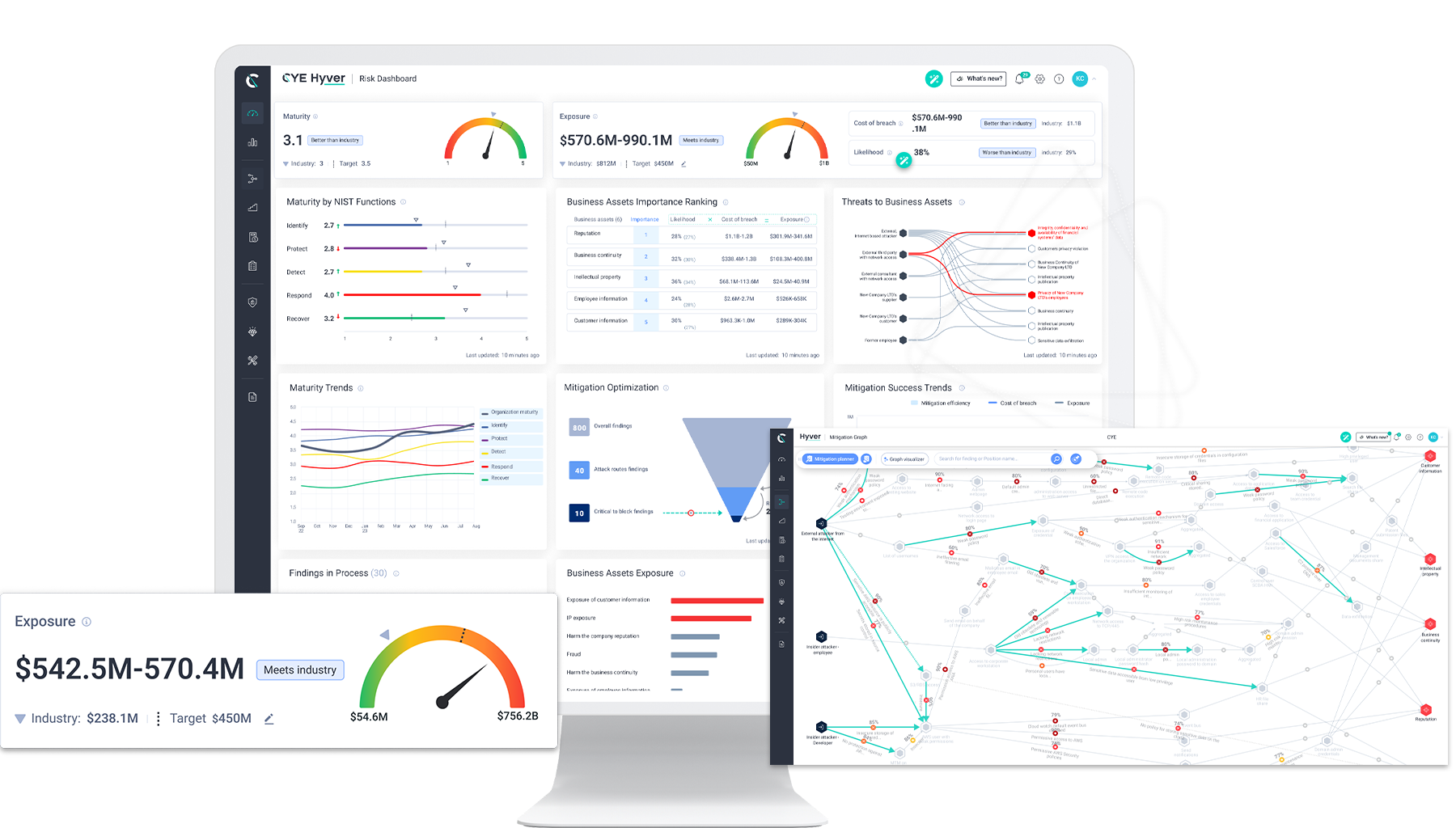

Get clarity on the financial value of your cyber exposure.

Mitigate the most likely attack routes to your business assets.

Identify weaknesses to strengthen your cyber posture.












Download this guide to learn how to present cyber risk to the board and win approval and support for cybersecurity initiatives.
Get the Full Guide