In 2021, one-in-six firms that experienced a cyber attack said they almost “went under,” according to the 2021 Hiscox Cyber Readiness Report.
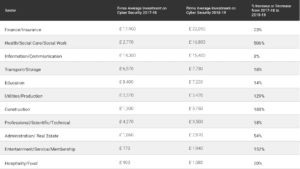
While certain sectors including energy, finance, and healthcare responded to the rising threat by increasing investment in cyber-security, recent surveys and UK government data show that food and beverage producers continue to lag behind. In fact, only 62% say it is a high priority, vs. 77% of businesses overall. They are also less likely than others to report having up-to-date malware protection (71%, vs. 83% overall) or network firewalls in place (66%, vs. 78% overall).
Food and beverage mafnucaturers remain a prime target for cyber-attack due to several factors, some of which are unique to the sector.
The food industry’s cyber risk factors
1. Insecure and outdated Industrial Control Systems (ICSs)
While the industry has seen major advances in digital technology to revolutionize food processing, they were not accompanied by security improvements. In fact, many food manufacturers still use legacy ICSs that are not configured to handle modern cyber threats. Even new ICSs are missing long-term cybersecurity protections and are unprotected from external access through third-party channels. Moreover, while most ICSs are inherently insecure, in the food industry, ICSs also have specific vulnerabilities, such as rigid controls that rely heavily on physical security.
2. Industry 4.0 and IT/OT Convergence
Being insecure-by-design, ICS is even more challenging to protect when introducing aggressive digital transformation initiatives, which are becoming increasingly common. These efforts improve efficiency, but also introduce an expanded attack surface, by enabling greater connectivity to the manufacturing network, which exposes it to both commodity malware from the IT network (insecure HMI interfaces) and targeted attacks.
3. Cybersecurity skill gap
Operations technology (OT) personnel, those responsible for operating and maintaining ICSs in the food manufacturing industry, are often experts trained in food safety and production — not in cybersecurity. Although ICS cybersecurity standards are well-documented, their complexity and volume overwhelm most food industry personnel. Research has also found that leaders in food processing and manufacturing are typically unaware of the extent of the cyber risk present in their industrial systems and OT/IT networks.
4. Lack of security maturity compared to other sectors
While other sectors focus on hardening security, in the wake of widely publicized cyber-attacks against them, criminals and threat actors move to still-vulnerable, lower-hanging fruit, making cyber immaturity a risk in its own right.
5. Covid-19 and the emerging cyber threat
The pandemic has forced businesses to operate remotely, expanding their attack surfaces and opening new doors for hackers to exploit vulnerabilities. In addition, food producers have had to innovate to keep pace with increased demand, with some introducing technological shifts that further increase the attack surface.
Potential cyber-attack consequences
The consequences of a successful attack on a food manufacturer could dwarf those in other sectors because disruptions to this industry not only interrupt business continuity and bankrupt the company, but also create contaminated food products that directly harm consumers. Food producers who underestimate the level of risk and damage that could be caused by a potential breach might face:
- Production line interruptions and shutdowns that could cripple the business
- Degradation of food products, making them unsafe for sale and consumption
- Financial loss as a result of ransomware pay-outs and loss of productivity
- IP breach of food recipes and production processes
- Physical harm to personnel and equipment
- GDPR violations resulting in fines
- Reputational damage
Steps for improving cybersecurity
In a new era in which cyber-attacks are more frequent and complex than ever, food producers must make cyber-security a top priority. Leaving digital communication platforms and production environments exposed to potentially devastating cyber-attacks is no longer an option. In the interest of both companies and consumers, food companies must acknowledge the increased risk and take immediate steps, including:
- Conducting comprehensive, end-to-end cyber risk assessments that include inventorying both ICS and IT systems continuously, to keep up with a rapidly changing attack landscape
- Tailoring such security assessments to food producers’ unique cyber risk environments by focusing on business-critical assets (i.e. production and IT/OT sensitive interfaces)
- Prioritizing remediation efforts based on a clear remediation plan that takes into consideration the likelihood of exploitation of the vulnerabilities and security gaps found in the assessment
- Fostering best practice communication routines between OT and IT security staff and integrating both processes and technology into internal communication protocols between teams
- Adopting and extending food safety and food defense culture and protocols to cybersecurity and acknowledging the risk posed to food safety by cyber attacks
- Increasing security vigilance and raising awareness regarding the cyber risk inherent to industrial sectors, in general, and to food producers, in particular
Editor’s note: this post was originally published in August 2020 and has been revamped and updated for accuracy and comprehensiveness.









