Mastering CTEM with Cye platform’s Exposure Assessment and Mitigation
Learn how Cye platform can help you master continuous threat exposure management (CTEM) so you can make better security decisions.
DOWNLOAD NOW
AI is leveraged across Cye's platform, accelerating time to identify exploitable vulnerabilities, mitigate likely attack paths, and continuously reduce your organization’s cyber exposure.
Book a DemoCreate a mitigation plan that increases my maturity level to the industry benchmark.
What is my organizational exposure?
Create a quarterly board report with my current data
Ask questions in plain language and get fast, grounded answers about exposure, attack paths, maturity, and mitigation strategies.
Cye AI lets you interact with your data in a secure environment – so you can ask questions without copying sensitive information into public tools.
As your personal cyber agent, it turns insights into board-ready reports, recommends practical mitigation steps, and helps you move from “what does this mean?” to “what do we do next?” based on your environment.
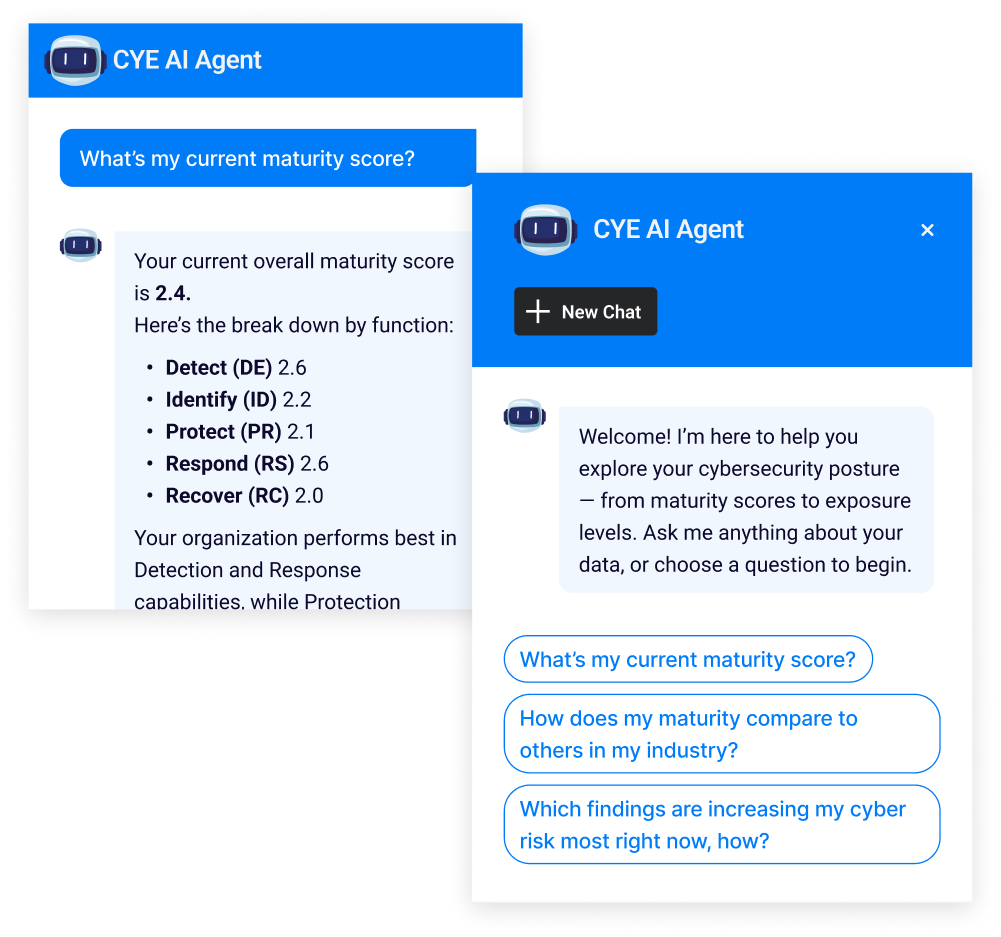
Make every pen-test and assessment report immediately actionable.
Import your existing reports in any format – PDFs, sheets, CSVs, and more – no cleanup or reformatting required. Cye AI automatically extracts findings, deduplicates results, and maps only what matters onto your organization’s attack graph – keeping exposure and maturity top-line metrics accurate and actionable, and revealing the attack vectors most likely to reach your critical business assets.
Integrations with your security tools are also faster and more effective than ever. AI automates mapping, deduplication, and correlation across sources – connecting the dots so you get a cleaner, more complete, and more actionable exposure view.
The result: you move from “we have data” to “we have clarity.”
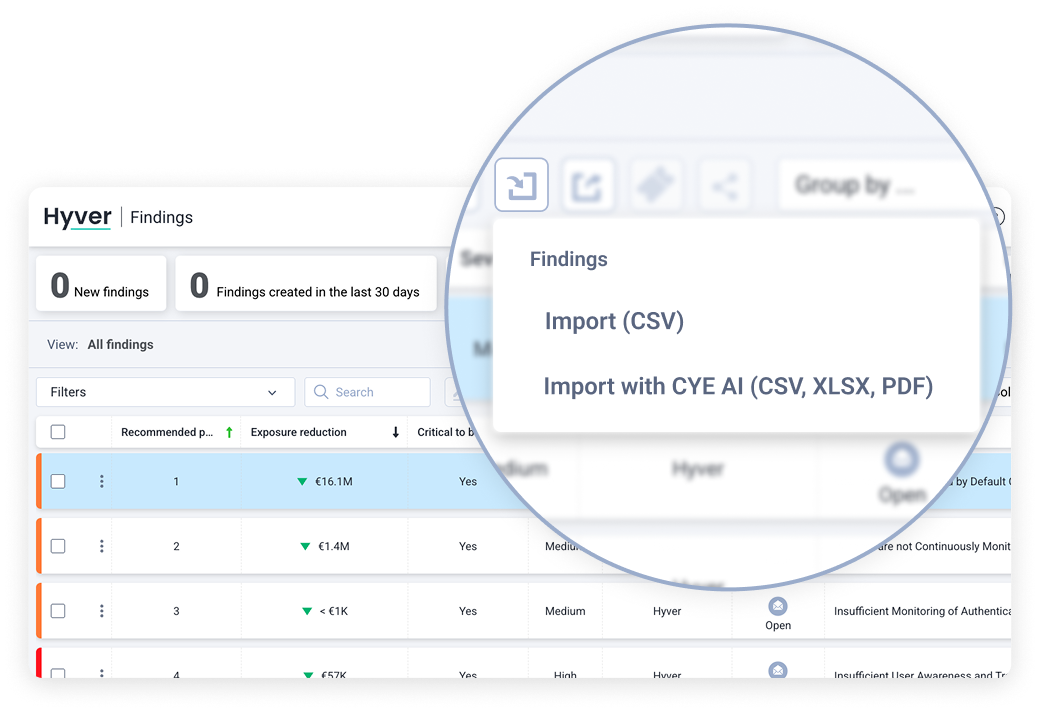
Turn ISO/IEC 42001 requirements into actionable risk mitigations.
With ISO/IEC 42001 mapped to NIST CSF, Cye helps you interpret requirements, organize evidence, and close gaps faster.
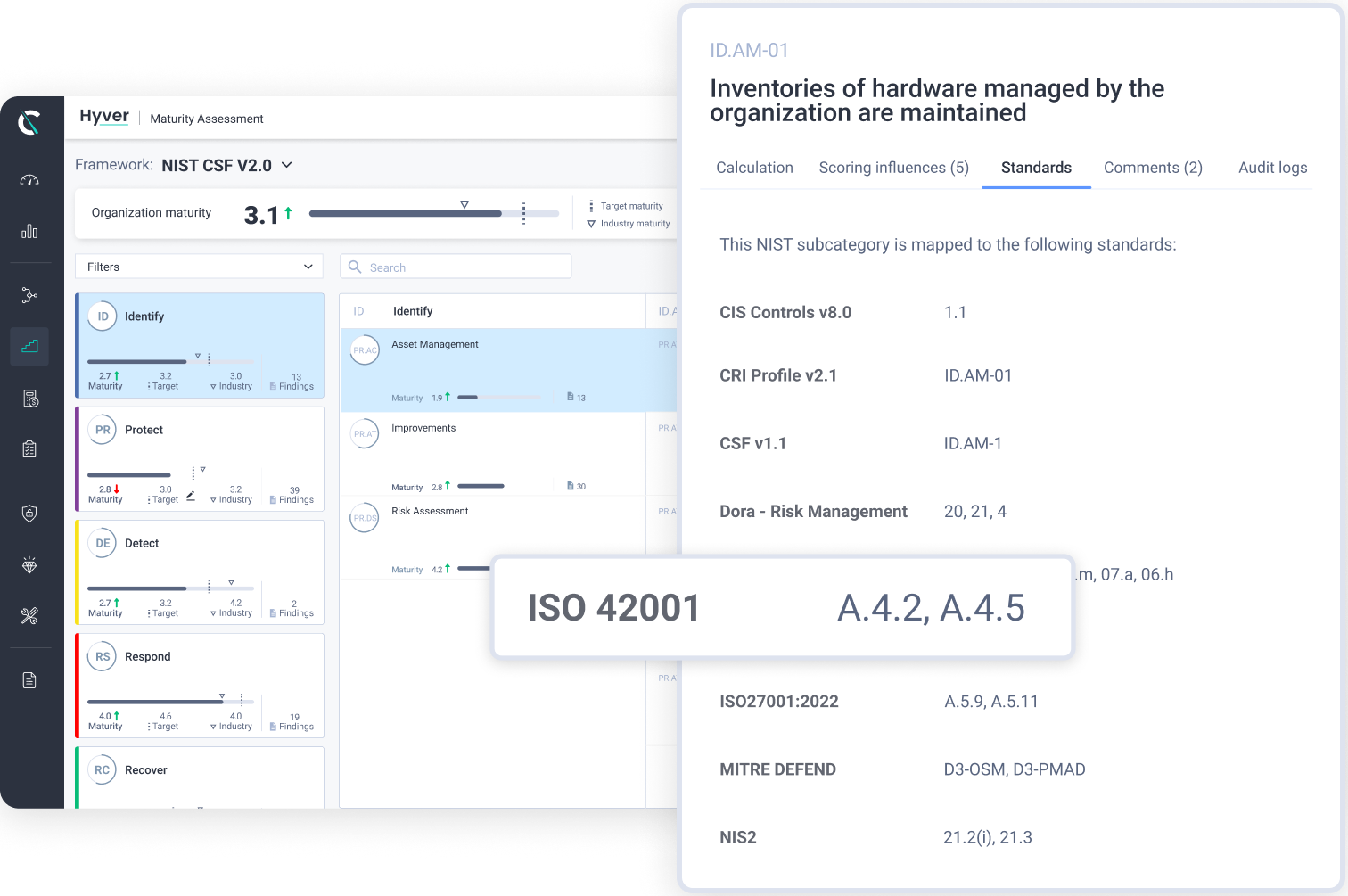
Know instantly what needs attention now – without digging through dashboards.
Major risk shifts and meaningful changes are instantly visible on your main dashboard. AI-powered highlights surface what materially changed in your organization’s risk and why it matters. Teams can dig deeper to understand the drivers, assess impact, and decide what to do next.
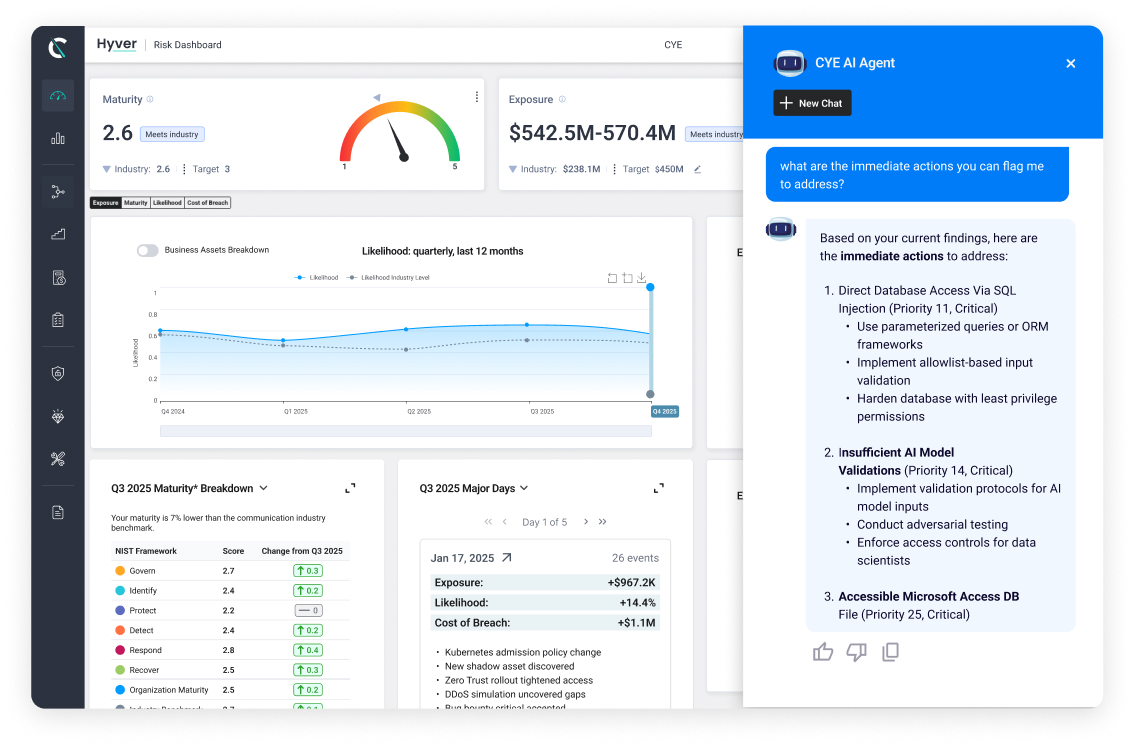
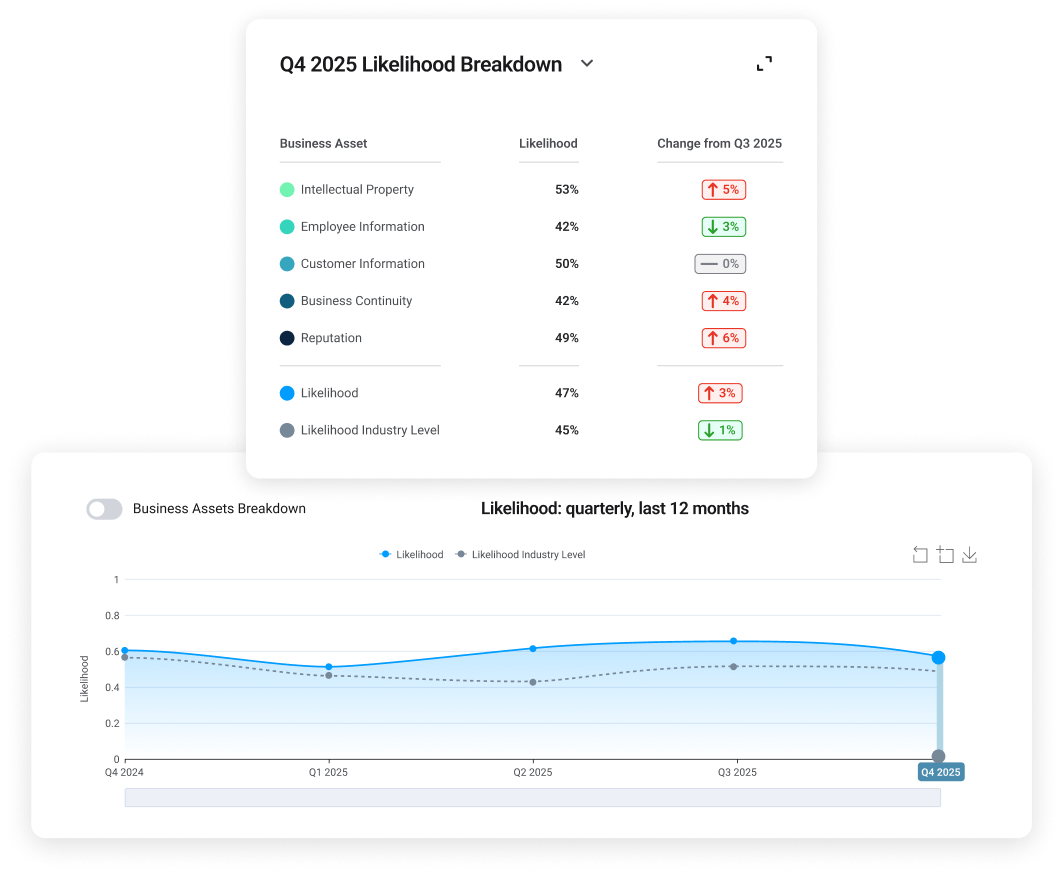
Cye’s exposure analytics use advanced math and machine-learning models to deliver predictable, explainable results based on real data. GenAI supports by gathering and validating the inputs; classical ML predictive models then produce the metrics with proven accuracy.
LoB is calculated via AI-driven data ingestion and Monte Carlo simulations to map critical-to-block paths.
CoB predicts financial impact using validated ML methods (e.g., linear regression, decision trees, random forests) trained on large-scale patterns – producing model-driven estimates, not generic ranges.
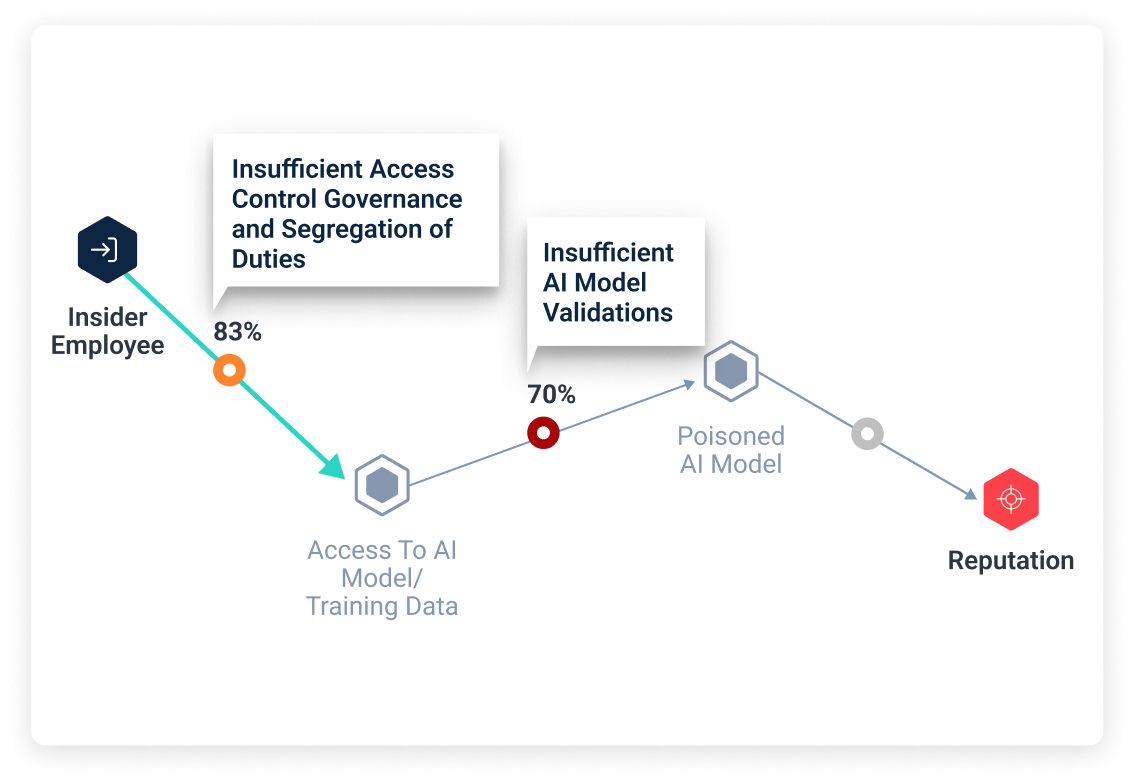
Reduce AI risk end-to-end with security posture assessments led by Cye’s elite cybersecurity experts.
We help you identify and reduce AI risk across the organization, secure AI use throughout the SDLC, and assess the security posture of internally developed LLMs.







Cye experts design, validate, and continuously improve the models behind Cye so recommendations reflect real attacker behavior and real-world constraints.

Your data stays your data.
Each customer’s information is isolated, never used to train public models, and processed inside Cye’s secured environment.

Cye AI runs on secured LLM infrastructure (e.g., AWS Bedrock) with RAG, strict guardrails, and agent separation to keep answers grounded and reduce off-target responses and cross-tenant leakage risk.